Introduction
There isn’t a week that goes by when you don’t hear about cybersecurity and how cybercriminals have bled another victim dry of money.
In this article, we’re going to outline the three most effective ways to secure your IT systems in your business and your personal life.
As a bonus, we promise not to make this too technical, and all the tips listed in this article won’t cost you a penny.
1. Cyber Awareness
People are by far the weakest link in any small businesses IT system. You could invest hundreds or even thousands in a new IT security system, and it could quite easily be bypassed by one of your colleagues that does not have an awareness of what to look out for in a classic phishing email.
Luckily the solution is simple, and it does not involve any investment, besides your time.
Just make sure you are running regular lunch and learns with your current technology provider. This can be as quick as a half hour session to go over the latest threats that may be landing in your inbox. Your IT/Technology provider will have a good idea of what this looks like as they’re dealing with cyber threats daily and are “in the know” on what to look out for.
2. Enforce multifactor login
Those in the know call this MFA or 2FA but we’re keeping this simple so multifactor login is a little more understandable. It’s making sure any of the cloud services your’e current utilizing are protected with two passwords and not just one.
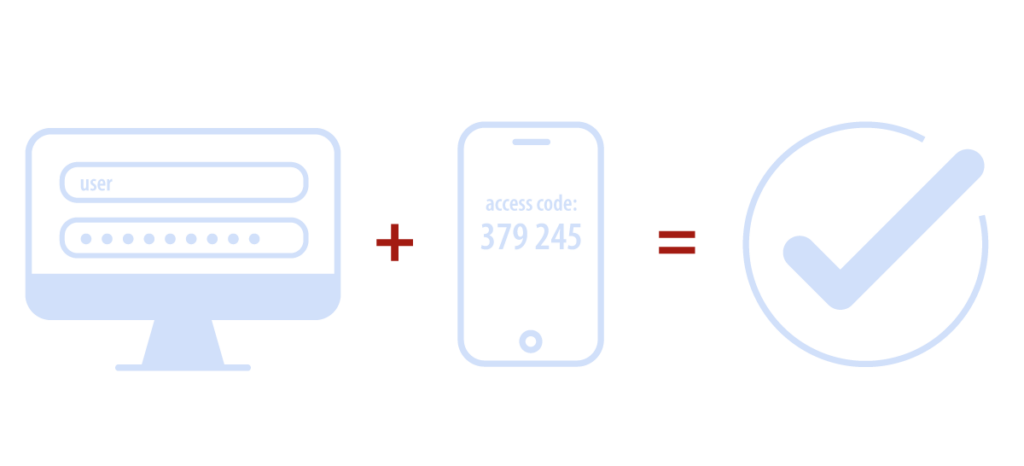
This is implemented by having a standard password and a secondary password which is authorized by your smartphone.
Running either an app on your phone or a text message that asks you merely to approve/deny the login to your cloud service when you are at the login page.
This is by far one of the best methods to protect against hackers as most hacks over the last 12 months have been to cloud services by cybercriminals pretending to login you into a genuine cloud service. Without access to your smartphone, they don’t have a chance of bypassing this multifactor login security.
3. Check your Backup service
You won’t believe how obvious this next tip seems, but how critical it is to ensure your systems are secure. If your IT systems do become victim to an attack, you may find that the only way to recover your systems is by changing passwords and restoring your files from a backup.
We’ve seen this one too many times to count from clients coming over to us in the past when a ransomware attack is deployed.
Their current IT provider fails at the most crucial stage and that is by backing up the company data correctly.
While the business may have backup software in place and it’s turned on, no one at the IT company has checked to see if files and data can be restored from the backup. And you don’t want to find out your backups don’t function as expected when they’re your only way of restoring your systems.
Please make sure that you can restore from a recent backup.
While these tips are great first steps to securing your IT systems, these are also the simplest and most obvious to implement. If you’d like to hear about some other crucial steps you can be implemented in your business that don’t require massive investment then please connect with us.
Get in touch with us
Secutor Cybersecurity is a trusted partner comprised of industry leading experts in the fields of Cybersecurity and Governance, Risk and Compliance. We partner with our clients to deliver on-demand solutions tailored to expertly navigate the regulatory demands of their specific industries.
Our proven track record of successfully exceeding client expectations is achieved through the combination of our methodical approach, advanced technologies, subject matter experts, and synergy with client team members.
Secutor is your team of world-class problem solvers with vast expertise and experience delivering complete solutions keeping your organization protected, audit-ready, and running smoothly.







